Password Recovery Experts
Your trusted partner in recovering lost Password, assets and navigating crypto scams effectively and efficiently.




Password Recovery Services
Expert assistance in recovering lost passwords for your cryptocurrency accounts across various platforms.




Secure Recovery Process
Our team ensures a safe and efficient recovery process for your crypto accounts and assets.
Password Recovery 101
A brief overview of how we perform password recovery.
We provide reliable solutions for password recovery, ensuring your digital assets are protected.
Trusted Solutions
Seed Phrase Recovery 101
A brief overview of how we perform seed phrase/ mnemonic recovery.
Step 1.
Extract a wallet backup
Our experienced team, lead by father son team Chris and Charles Brooks, will guide you through retrieving your encrypted wallet backup.
Step 2.
Collect password guesses
Next, you will provide our team with a list of password guesses that you think are related to the actual wallet password. As many, or few, guesses as you'd like. The more guesses provided, the better our chances of success.
Step 3.
Brute-force the password
Your sensitive wallet details will be moved, by hand, to an air-gapped network of GPU powered password cracking servers.
Our experienced team will use proprietary techniques to recover your wallet password with a 87% success rate.


Step 1.
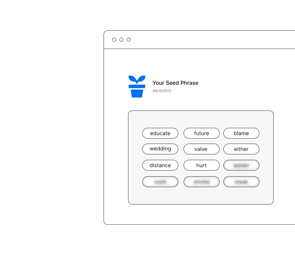
Collect the seed guess
Whether you're missing a few words or have uncertainty about your entire 12-word seed phrase, our process begins with our technicians carefully documenting the parts of the seed you do remember. This initial step is crucial for narrowing down the possibilities and streamlining the recovery process.
Step 2.
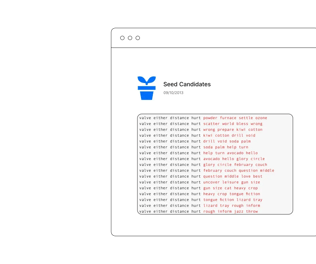
Calculate potential permutations
Next, your sensitive seed details will be moved, by hand, to a network of secure air-gapped servers specialized for seed recovery.
Using the known pieces of the seed phrase, our team will calculate the potential permutations of seed phrase combinations, building a candidate list typically over 1 billion seeds long.
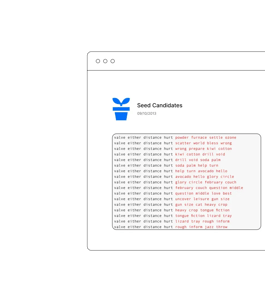
Step 3.
Test the seed candidates
Once we've assembled the seed candidates, our GPU servers begin their rapid testing process. Each potential seed is used to generate a series of addresses, which are then cross-checked against the target address. This cycle continues swiftly until our system pinpoints the correct seed, efficiently recovering your access.